Getting Started
From Burstcoin security to wallet selection, the Getting Started guide provides the information needed to succeed.
Software
The definitive collection of open-source and easy to use software is located in the Burstcoin Software Library.
Documentation
Visit the Burstcoin Documentation Project for more information. Contribute new documentation or recommend improvements.
Faucets
Activate a new wallet for mining or to receive a transfer from Bittrex. Visit the Burstcoin Community Faucet list.
FAQs
Supporting new users, this section contains Frequently Asked Questions. Help curate by visiting the documentation section.
You are in the right place! Be sure to read these sections carefully and ask for assistance if there is anything that you do not understand.
The first choice to make is to select a wallet. However, if you are new to cryptocurrency, please read the sections related to security below.
- Phoenix is the newest and easiest wallet to install. As a lite-mode wallet, it does not maintain a complete copy of the Burstcoin blockchain. Unless you want to operate a full node, or need specific features that are not included, this is the recommended wallet. Basic features are included, and additional features are added on a regular basis. Phoenix is a cross platform application and can be installed on all major operating systems.
- BRS (Burst Reference Software) is the wallet required if you want to operate a full node. It maintains a copy of the complete Burstcoin blockchain. Versions of the BRS software are available for Windows (64-bit version only), MacOS, Linux, Android, and Docker.
To download and install a Burstcoin wallet, visit the Burstcoin Software Library. The library is a comprehensive collection of Burstcoin software and includes mining software, plotting software, pool software, dApps, and many other useful tools.
Activate your account
New Burstcoin accounts have a default 64-bit level of security prior to activation. At this level, two different passphrases can produce the same Burstcoin address (see The Reed-Solomon Address Format under Core features for more information). Full security, at the 256-bit level, requires an account to be activated on the blockchain with a public key. “Activating a Burstcoin account” propagates an accounts’ public key to the network. Common ways to do this include clicking on “Set account info”, “send a message”, “buy an alias”, “set reward assignment”, or “send BURST” to create an outgoing transaction. If you are just getting started, you will need to secure a small amount of Burstcoin in order to complete this first outgoing transaction. This is easily accomplished by visiting one of the community provided Burstcoin faucets or by requesting the amount necessary on one of the Burstcoin forums. This type of request is usual and encouraged.
FAQ - How can I obtain Burstcoin to make my first outgoing transaction?
Note: There is an alternative method for activating an account without the need for an outgoing transaction. It is quite technical, and not intended for the beginner level user. For more information if desired, see Activate a Burstcoin account using the Burst API.
Figure 1:
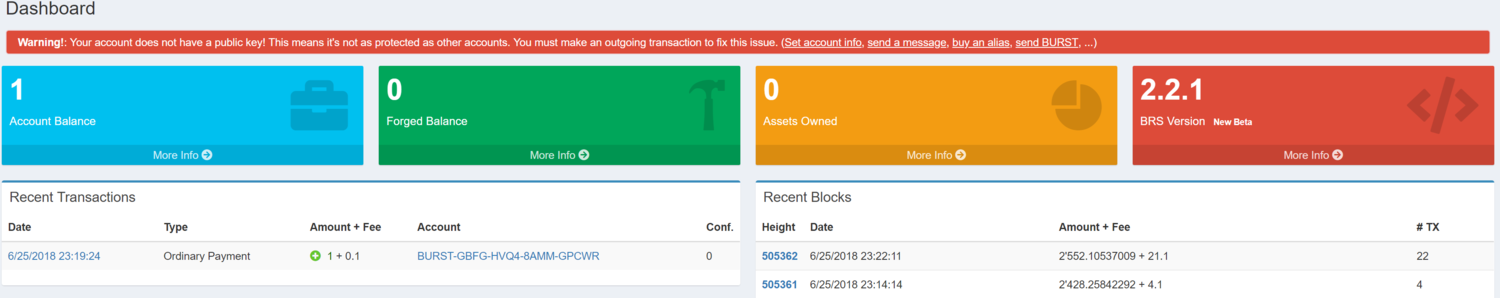
Security implications of blockchain based cryptocurrency
It is important to understand the security implications of Burstcoin being a blockchain based currency. Burstcoin accounts are secured by a single passphrase (sometimes referred to as a private key) which can be thought of as a very secure password. If you cannot produce your passphrase, you cannot access your Burstcoin account and your coins will be effectively lost. There is no central organization that exercises custodial control over accounts, so there is no one to contact if you forget, lose, or otherwise fail to protect your passphrase. There is also no pass word reset option, so extra care must be taken when creating an account and preserving a record of its passphrase. In cryptocurrency, there is a concept referred to as “burning” coins. This is a deliberate process of transferring coins to a wallet with an unknown passphrase in order to permanently reduce the circulating supply. In effect, losing your passphrase has the same effect.
Accounts secured by a single passphrase are commonly referred to as “brain wallets” because the passphrase is the only identification necessary for making transactions. There are no additional hardware or software requirements of any kind.
The chances of forgetting or losing your passphrase is much higher than having your password stolen. However, it is vitally important to set up your account carefully and only use computer equipment that is secure from intrusion.
The best way to preserve your passphrase is to store it securely in more than one location. If you will be storing your passphrase on a computer or other hardware, it is important to maintain a backup copy of your files in another location in order to protect against equipment failure.
- If stored on a hard drive – the hard drive might crash.
- If stored in a password manager – the password file may become corrupt or be deleted.
- If printed on paper – the paper might be destroyed in a fire or be misplaced.
- If committed to memory - it might be forgotten.
The same care given to creating accounts and preserving passphrases should also be followed when making transactions. Burstcoin transactions are not reversible. If you accidentally transfer Burstcoin to an account with an unknown passphrase, there is no way to retrieve the coins.
Associating the full value of your account with your passphrase is a useful way to determine the appropriate level of security for protecting its passphrase. For accounts with higher values, more extensive measures should be used.
Eventually, you will have to enter your passphrase on a local computer in order to sign transactions. Before doing so, be certain that the computer is safe from intrusion. This means that you must be certain that your computer has not been compromised with malicious software that could be logging keystrokes.
To maximize security, always follow these best practices:
- Use official Burstcoin wallets only.
- Use the 12-word passphrase that is automatically generated during the account registration process in order to avoid Brute Force and Rainbow Table attacks.
- If any modification is made to the passphrase, only add additional characters. The length and complexity of the passphrase should never be reduced. A minimum of 35 truly random characters provides an adequate level of security.
- Avoid special characters which can create confusion and are completely unnecessary. If adding special characters, use ASCII code representations rather than Unicode characters. Example: For the double quote character, use ASCII code 34 (0x22) rather than one of the various Unicode characters which are not interchangeable. Microsoft Word uses Unicode characters by default, so this program is not ideal for composing or storing passphrases which contains special characters.
- Do not share your passphrase with anyone that cannot absolutely be trusted.
- Do not store your unencrypted passphrase on a remote node or your local workstation.
- Use special care when connecting to remote nodes.
- Do not leave a printed copy of your passphrase next to your computer.
- Use accounts with smaller balances for daily operations. Only access higher balance accounts when necessary and with special attention to security.
- A password manager which stores multiple encrypted passwords under a single database password can be secure and convenient. KeePass is a free open source option.
- Activate your account with an outgoing transaction. This will increase your encryption level from 64-bit to 256-bit immediately.
Burstcoin's automatically generated passphrase
Centralized organizations limit the number of login attempts to the accounts that they provide and do not disclose their authentication algorithm publicly. Otherwise, their short passphrases would be discovered in a matter seconds or minutes. The open source nature of the Burstcoin client allows an unlimited number of login attempts which can be executed very quickly at rates reaching billions of login attempts per second. Because of this, the Burstcoin account registration process automatically generates passphrases that are very long and complex.
To a first time user, a passphrase generated using a set of predefined publicly available words may seem counter-intuitive.
The number of passphrases that can be generated from Burstcoin’s list of 1,626 words in 12-word combinations, is 341,543,870,028,173,427,817,970,975,906,355,941,376. This number can be represented as 341undecillion, or 341 billion billion billion billion. This is euphemistically called a “large number” in mathematics. It is difficult to imagine because it is astronomically large. Attempting all possible combinations of a 12 word passphrase drawn from this known dictionary (a process known as brute forcing), would, on average, take billions of billions of years. Just 5 Words would take over 2,000 years. Each additional word increases the difficulty by 1,626. In conclusion, attempting a brute force attack on a Burstcoin passphrase would be an exercise in futility.
| Number of Words | Possible Passphrase Combinations | Bits of Entropy |
|---|---|---|
| 1 | 1,626 | 10.66 |
| 2 | 2,643,876 | 21.33 |
| 3 | 4,298,942,376 | 32 |
| 4 | 6,990,080,303,376 | 42.67 |
| 5 | 11,365,870,573,289,400 | 53.34 |
| 6 | 18,480,905,552,168,500,000 | 64 |
| 7 | 30,049,952,427,826,000,000,000 | 74.67 |
| 8 | 48,861,222,647,645,100,000,000,000 | 85.34 |
| 9 | 79,448,348,025,071,000,000,000,000,000 | 96 |
| 10 | 129,183,013,888,765,000,000,000,000,000,000 | 106.67 |
| 11 | 210,051,580,583,132,000,000,000,000,000,000,000 | 117.34 |
| 12 | 341,543,870,028,173,000,000,000,000,000,000,000,000 | 128 |
Your wallet is safe with a 12-word auto generated passphrase. Adding capital letters, numbers, or symbols would make the passphrase exponentially harder to crack, but the auto generated passphrases are already more than sufficient. In the mobile wallet provided by the PoC Consortium, an even larger set of words is used.
https://burstcoin.ist/2017/10/07/is-the-automatically-generated-passphrase-secure/
Burstcoin Wallets
If you already familiar with the concept of a cryptocurrency wallet, and are just looking for the Burstcoin wallets, they are located in the Burstcoin software library. However, if you are new to cryptocurrency in general, it is recommended that you continue reading to gain a bit of understanding first.
Burstcoin wallets do not contain Burstcoin. This is a common misconception. Burstcoins exist only on the Burstcoin blockchain, a shared public ledger. A wallet is a software program that interacts with the blockchain. It reads blockchain data and displays information that is relevant to account holders such as balance, transaction history, messages, products listed for sale on the asset exchange, etc. Transactions, which move Burstcoin from one account to another, are initiated using wallets.
A Burstcoin wallet may be thought of as the user interface for the Burstcoin blockchain.
Burstcoin wallets use an account’s public address (public key) to determine what information from the ledger and mempool to display in the wallet. There are no records that relate a public address to a particular account holder in a personally identifiable way. Personally identifiable information can be disclosed in the normal course of business however, such as when ordering a product and providing a shipping address. Unless an account holder initiates such a disclosure, there are no other ways to identify the account holder for a particular public address. For this reason, many choose to maintain several accounts, each for a particular purpose.
Each Burstcoin account has a passphrase that is known only to the account holder as long as it is not disclosed. There is no record of this passphrase in the wallet. The passphrase is entered into the wallet each time a transaction is authorized, but it is not retained by the wallet. Transactions which are broadcast to the network also do not contain the passphrase. When a transaction is broadcast, it contains a single-use digital signature. It can be derived from the signature, using cryptology, that the transaction was created by the owner of the passphrase for the account which created the transaction. The actual passphrase cannot be derived from the signature however.
If a wallet (software program) is loaded onto a computer and the computer is lost or destroyed, the Burstcoin in the owner’s account on the blockchain is not affected. Provided that the account owner is still in possession of the account’s passphrase, a new wallet can be installed and the passphrase will restore full access. Passphrases work in any wallet, new or old, local or online.
Wallets are continually upgraded to incorporate useful new features and to make the incredible power of the Burstcoin blockchain more fully accessible.
There are several types of Burstcoin wallets. Over time the selection of types will increase as well as combinations and collections of desired features. Currently, there are local, online, and mobile wallets.
Local wallets should reside on computers that are secure from intrusion. For particularly large balances, the local wallet can be maintained on an air-gapped computer so that the passphrase is never exposed to the internet. Burstcoin’s offline transaction signing makes this possible.
Online wallets are centralized. That is to say that they are provided as a service by certain community members. As cryptocurrency is intended to be a trustless money system, this makes them less than the ideal, but convenient for certain situations. Entering your passphrase into an online wallet exposes it to the internet. There is also no way to verify that the operator has not made a record of your passphrase. If you use an online wallet, it should be for a distinct account. Do not access your local wallet through an online wallet. This is possible, but strongly discouraged. Doing so reduces the security of your local wallet to that of an online wallet. There are however several use cases for online wallets:
- Maintaining a small balance for daily purchases.
- Using an online wallet to collect mining proceeds which are then transferred to a more secure software wallet.
Editors note: There are risks associated with online wallets such as disclosing your account’s passphrase to the online wallet host. In addition, if an online wallet does not employ SSL technology, there is a chance that your account’s passphrase could be intercepted by a third party. For these reasons, online-wallets, while available, are not recommended. If you choose to use an online wallet, only use wallets provided by reputable community members or organizations.
Each Burstcoin wallet acts as a network node, a computer that runs the Burstcoin network by relaying collected information to other nodes. The nodes are thus in a continual state of synchronizing. All nodes support the network in this relay of information. At the election of the node’s owner, some participate in a competitive process to group transactions and commit them to the blockchain. This process is referred to as mining. For more on this optional process, see Burstcoin mining.
Burstcoin’s vision for Security
Burstcoin security entails much more than passphrase and wallet security. From its inception, Burstcoin has sought to enhance faster adoption of blockchain technology while guaranteeing optimal security in all aspects of it operation. It was created in 2014 when attacks on cryptocurrency networks were already common. To keep the Burstcoin network safe, certain strategies were employed by the development team.
- Collusive nodes attack (51%): This attack happens when a majority of nodes conspire to harm a network. To prevent this, Burstcoin uses Byzantine fault-tolerance technology to help build dependable protocols. The focus is on identifying honest nodes by setting an upper boundary for maximum tolerance.
- Denial of service attacks (DDOS): Burstcoin employs a Dymaxion design that requires all nodes to perform PoC (proof-of capacity) validation. It also carries out regular vetting to identify and blacklist misbehaving nodes.
- Progressive network updates: The nature of threats to cryptocurrency networks change rapidly. The development team has adopted a system of progressive improvement that involves constant checks to identify and fix gaps.
- Advanced encryption: To keep details and funds free from third-party entities and attacks, the Burstcoin network employs advanced encryption. Even when sending funds on the network, details are not easily revealed.
Note: Most cryptocurrency losses reported in the blockchain sector occur on exchanges. The Burstcoin development team created a decentralized asset exchange that makes it possible to bypass centralized exchanges. Based on this technology, a decentralized exchange (DEX) operated by Burstcoin is in the planning stages.